Your IoT ecosystem is not just a collection of devices; it is the backbone of your operations, and every connection matters. Secure your connected devices and infrastructure with /IoTConnect™ Secure - a comprehensive, layered security framework designed to protect your IoT ecosystem from design to deployment.
/IoTConnect™ is engineered to deliver security from the ground up, blending hardware-rooted protection with zero-trust architecture. Whether you are building a simple proof of concept or deploying at industrial scale, /IoTConnect™ Secure provides the right balance of cost, complexity, and risk mitigation to match your needs.
/IoTConnect™ offers a robust suite of features designed for secure IoT deployment and management. Explore these features to ensure your IoT ecosystem remains protected from emerging threats.
Ensures that data is encrypted during transmission and storage, safeguarding sensitive information from unauthorized access.
Implements granular access permissions based on user roles, ensuring secure and controlled access to critical resources.
Enables Over-the-Air (OTA) updates with built-in validation mechanisms to protect devices from malicious or unverified updates.
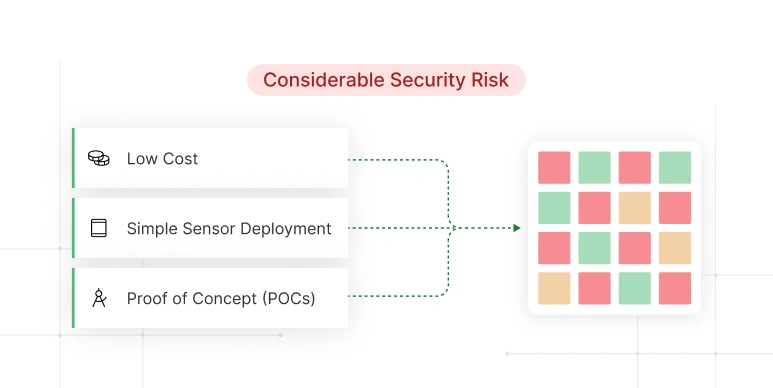
For initial, low-cost implementations where there is no security, but functional for proof-of-concept (POC) environments.
Ideal for simple sensor deployments with no security requirements.
Token or x509-based authentication using generic crypto libs.
Entry-level solutions that do not require advanced security features.
Not scalable, best suited for limited applications and POCs.
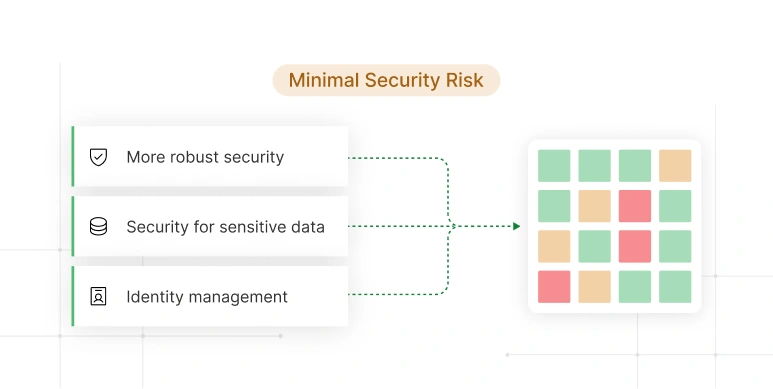
Designed for more complex environments, offering enhanced security features for broader deployments and scalability.
Leverages technologies like Trust Zone to provide a level of separation and security for sensitive data.
Secure management of digital certificates to protect data integrity and identity validation.
Suitable for applications requiring more robust security without compromising on performance or scalability.
A comprehensive security model for mission-critical applications where data confidentiality, integrity, and availability are paramount.
Secure separation of critical data within the device itself, reducing exposure to risks.
Adds an external layer of protection to safeguard keys and sensitive data, ensuring optimal security.
Built-in secure communication protocols from the supplier ensure safe data transfer and encryption.
Highest level of x509 certificate management, utilizing hardware-based security elements for best-in-class authentication.
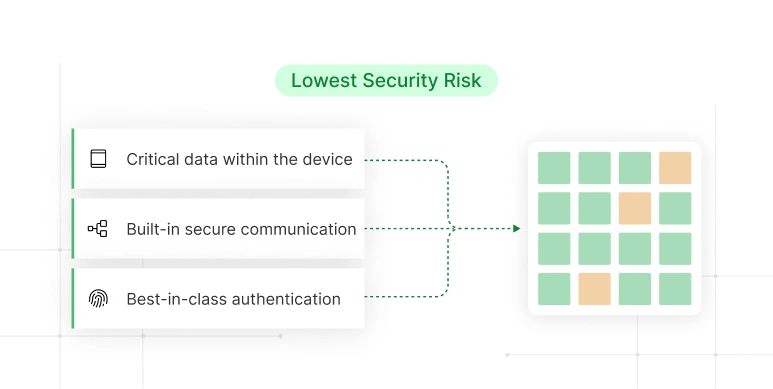
/IoTConnect™ Secure supports all levels of device security maturity, helping you build confidently regardless of your current stage or design strategy.
| Level |
|
|
|
|---|---|---|---|
| Cost |
|
|
|
| Complexity |
|
|
|
| Risk |
|
|
|
No matter where you are in this continuum, /IOTCONNECT Secure helps you scale securely.

These questions help determine your ideal point in the security-cost-risk trade-off, also known as the "Pick 2" Dilemma - choose between time, cost, and risk, but rarely all three.
Digital certificates are at the core of trusted IoT communication. /IoTConnect™ Secure offers full lifecycle support for X.509 certificates to ensure that your devices stay trusted throughout their operational lifespan.
This automation ensures your PKI policies stay compliant and minimize manual certificate handling across large fleets.
Onboard devices at scale with secure, policy-based certificate enrollment.
Schedule and automate certificate refresh to avoid downtime and prevent expiration-related breaches.
Instantly revoke compromised or retired device certificates and issue new credentials.
Support secure re-provisioning of certificates as devices change hands.
/IoTConnect™ Secure is built on a Zero Trust Architecture, ensuring nothing is implicitly trusted - every device, connection, and transaction must be authenticated and authorized.
Transform your IoT ecosystem with secure, seamless, and intelligent solutions
Sign-Up TodayIf you already have a Certification Authority (CA) or Trust Authority in place, we can integrate with your existing system to enhance security. If not, we can help you set up a trusted environment.
Data integrity is vital for protecting the authenticity of the information your devices exchange. /IoTConnect™ offers encryption and secure communication protocols, such as TLS and VPNs, to ensure data is transmitted safely without tampering.
Device authentication ensures that only trusted devices connect to your network. We can help implement x509 certificates, token-based authentication, or secure key management systems for reliable device authentication and authorization.
Yes, remote management of security patches and firmware updates is essential for maintaining up-to-date protection. We provide secure and efficient methods to deploy updates across all your connected devices, ensuring they stay protected against new vulnerabilities.
Hardware-based security (such as Secure Elements) provides a physical layer of protection for sensitive data and cryptographic keys, while software-based security relies on encryption and software solutions. Depending on your device's requirements, we can recommend the best option for your security needs.
Regular security assessments, vulnerability scanning, and penetration testing are essential to identifying and addressing potential risks. We also recommend utilizing secure boot processes and hardware isolation to prevent unauthorized access to your devices.
Compliance with data protection regulations, such as GDPR or CCPA, is crucial when handling personal or sensitive data. We help ensure that your IoT devices meet necessary compliance standards through encryption, secure data storage, and access controls.
Credential management is a core aspect of IoT security. We provide tools to securely store and manage device credentials, including encryption and hardware-based solutions like TPM (Trusted platform modules), ensuring your devices remain secure against unauthorized access.